 CenterClick NTP200 Series Documentation - Client List
CenterClick NTP200 Series Documentation - Client List
Main
Store
NTP2xx Docs
o Features
o Hardware 200/250
o Hardware 220/270
o Getting Started
o Release Notes
o Front Panel Button
o Front Panel LEDs
o USB Console
o Admin CLI
o Using HTTPS
o SSH Authentication
o Client List
o Antennas
o Troubleshooting
o Graphs
o PPS Output
o Reimage 200/250
o Reimage 220/270
GPS14x Docs
Live Demos
Contact Us
Feedback and Bug Reports
Follow us on LinkedIn
Privacy Policy
Shipping and Tax
Returns and Warranty
Understanding the NTP Client List
All NTP clients that send packets to the device are tracked so you can determine who is querying your device.
Age-out and Limits
Each client IP is tracked and aged out after 7 days of inactivity.
The device can track 100,000 or more clients depending on model. If that limit is reached, the 7 day age-out time will by dynamically reduced in an attempt to clear out old entries.
The client tracking data is saved and restored on a controlled reboot, shutdown, and upgrade. However, if the device has been powered off for many hours, power cycled without a proper shutdown, or an unexpected time step occurs while running, the saved state is discardeded.
Sorting
Use the ![]() and
and ![]() buttons to sort the client list ascending or descending.
buttons to sort the client list ascending or descending.
Download and Export
The client list is available on the web interface, but also available for download in JSON and CSV formats. To see example data, just visit the Live Demos.
Entry Details
Each client entry records 8 pieces of data:
- The Client IP
- The Client Reverse DNS Entry (if enabled)
- First packet time
- Last (most recent) packet time
- RX packet count
- TX packet count
- RX packet flags
- TX packet flags
Using the above data, 2 additional items are computed:
- The RX packet frequency
- Any alerts
The RX frequency (called 'RX Every') is simply the average amount of time between each received packet over the entire lifetime the Client has been known
Each entry can be in one of 4 alert states:
- No alerts
 Sleep alert: a client hasn't been heard from in more than 2x its expected RX frequency (subject to some bounds)
Sleep alert: a client hasn't been heard from in more than 2x its expected RX frequency (subject to some bounds)
 Yellow alert: a client is sending way more packets than are responded to (likely rate limit) or the rx frequency is very short
Yellow alert: a client is sending way more packets than are responded to (likely rate limit) or the rx frequency is very short
 Red alert: a client appears to be blocked due to ACLs or sending only invalid packets
Red alert: a client appears to be blocked due to ACLs or sending only invalid packets
DNS Lookups
The device will perform reverse DNS lookups in the background for all clients that send requests. These lookups are rate limited to at most 1 lookup per second and are refreshed at most once per day.
The DNS lookup functionality can be disabled using the Admin Console if not desired. Lookups are also automatically suspended if the device has more than 50000 clients.
Packet Flags
A set of flags is stored for each client in each direction (RX and TX). For each RX and TX packet, flags are computed from the packet content and are OR'ed with the stored flags from every previous packet. Only the OR'ed flags are stored so the flags shown is a union of all packets for that client since client tracking began for that client.
The individual flags are currently (this is subject to change in future software releases):
| Flag | Meaning |
|---|---|
| T | Truncated packet (ex: short UDP) |
| 1 | NTP Version 1 |
| 2 | NTP Version 2 |
| 3 | NTP Version 3 |
| 4 | NTP Version 4 |
| V | Other NTP Version (Not 1-4) |
| A | NTP Mode Symmetric Active |
| P | NTP Mode Symmetric Passive |
| C | NTP Mode Client |
| S | NTP Mode Server |
| B | NTP Mode Broadcast |
| N | NTP Mode Control |
| M | Other NTP Mode |
| D | NTP KoD 'AUTH' |
| Y | NTP KoD 'CRYP' |
| R | NTP KoD 'RATE' |
| * | NTP REFID Matches Our IP (RX only) |
Examples
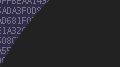
The below example from the Live Demos and some clients have come and gone idle causing Sleep alerts, but otherwise all is well.
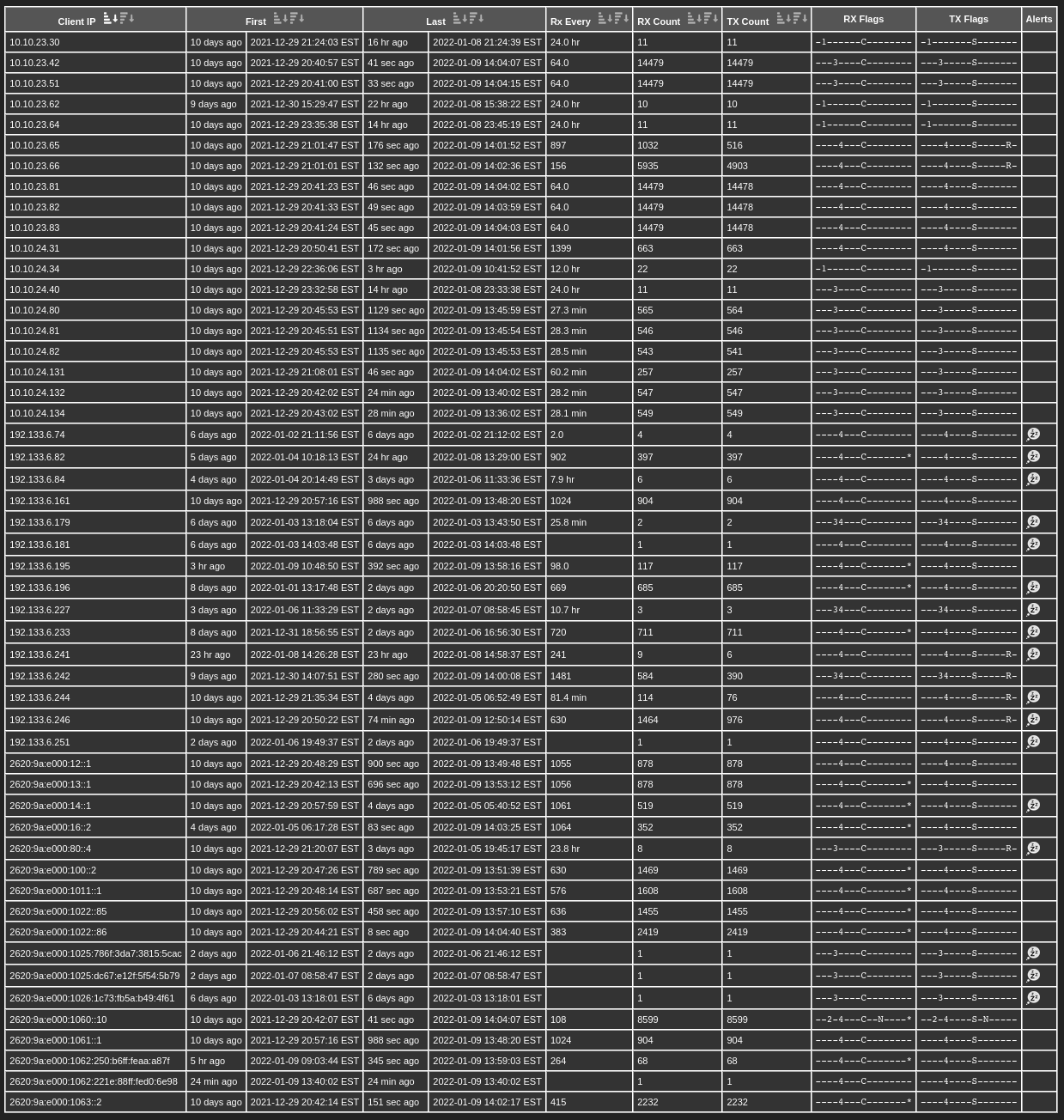
The below example from an Internet exposed and NTP Pool registered NTP250 and includes both well behaved clients but also DDoS attack attempts. This appliance receives over 2 million unique clients IPs per day, most of which are only active for a few hours. Sorted by descending RX Count we can see some frequent (<30 second) clients, but also some DDoS attempts using spoofed source IPs. In the latter we can see that the rate limiting algorithm has blocked the DDoS attempts and only responded a few times.