 CenterClick NTP200 Series Documentation - Using HTTPS
CenterClick NTP200 Series Documentation - Using HTTPS
Main
Store
NTP2xx Docs
o Features
o Hardware 200/250
o Hardware 220/270
o Getting Started
o Release Notes
o Front Panel Button
o Front Panel LEDs
o USB Console
o Admin CLI
o Using HTTPS
o SSH Authentication
o Client List
o Antennas
o Troubleshooting
o Graphs
o PPS Output
o Reimage 200/250
o Reimage 220/270
GPS14x Docs
Live Demos
Contact Us
Feedback and Bug Reports
Follow us on LinkedIn
Privacy Policy
Shipping and Tax
Returns and Warranty
Using HTTPS
By default HTTP is enabled, however HTTPS is not due to the requirement of HTTPS certificates.
Several methods are supported for configuring HTTPS certificates. Once enabled, all HTTP requests will be redirected to HTTPS.
Certificate Methods
Enabling HTTPS is located under the services menu on the admin console. 3 methods are supported:
NTP250> conf services Configuring Services... Service Commands: exit Exit Service Menu no http Disable HTTP interface https Enable HTTPS interface location privacy Enable Location Privacy on HTTP ssh Enable SSH NTP250[srv]> https Enabling https interface... To enable https interface you must obtain TLS certs using one of the following methods: H) ACME HTTP-01 method (needs outbound HTTPS & inbound HTTP/S) D) ACME DNS-01 method (needs outbound HTTPS & dynamic DNS) M) Manually upload a cert/key q) abort For more information see the HTTPS docs at https://centerclick.com/ntp Method? [H/D/M/q]
Let's Encrypt HTTP-01 method
This the easiest method to support, however it is only applicable if:
- The device has a public IP
- Inbound HTTP & HTTPS access from the Internet is allowed
- Outbound HTTPS to Internet is allowed
Method? [H/D/M/q] H To use Let's Encrypt HTTP-01 method you will require: * An administrative contact email address * A public hostname for this device * Inbound HTTP/S from the Internet * Outbound HTTPS to the Internet You can also specify a custom ACME URL for private usage For more information see the HTTPS docs at https://centerclick.com/ntp Continue? [y/n] y Contact Email: admin@example.com ACME URL (leave blank for Let's Encrypt): HTTPS Hostname: ntp1.example.com Alt HTTPS Hostnames (if any, comma sep): ntp1.example.net,ntp1.example.org Contact Email: admin@example.com ACME URL: HTTPS Hostname: ntp1.example.com Alt HTTPS Hostnames: ntp1.example.net,ntp1.example.org Continue? [y/n]
If the device has multiple DNS hostnames, you can enter a list of Alternative names and a certificate will be generated covering the primary hostname plus any alternatives. Alternatives should be comma-separated if needed.
Let's Encrypt DNS-01 method
If the HTTP-01 method is not possible, the DNS-01 method can be used instead. It is only applicable if:
- The device has a public DNS name, however a public IP is not needed
- Outbound HTTPS to Internet is allowed
- A Dynamic DNS service is available (not necessarily in the same zone as the public DNS name)
This method is ideal for devices that use private IPs and have no inbound Internet connectivity. DNS records are used to validate the domain ownership. For example the simplest case is:
| DNS Entry | Type | Value | Dynamic/Static |
|---|---|---|---|
| ntp1.example.com | AAAA | 2001:db8:881:3::100 | Static |
| _acme-challenge.ntp1.example.com | TXT | (generated) | Dynamic |
Method? [H/D/M/q] D
To use Let's Encrypt DNS-01 method you will require:
* An administrative contact email address
* A public hostname for this device
* A public Dynamic DNS service (with or without TSIG)
* Outbound HTTPS to the Internet
You can also specify a custom ACME URL for private usage
For more information see the HTTPS docs at https://centerclick.com/ntp
Continue? [y/n] y
Contact Email: admin@example.com
ACME URL (leave blank for Let's Encrypt):
HTTPS Hostname: ntp1.example.com
DDNS Hostname (if non-standard):
Alt HTTPS Hostnames (if any, comma sep):
DDNS Nameserver (if non-standard):
Copy/Paste full DDNS TSIG key (if needed), use <CTRL-D> to finish:
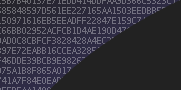
key "example-test" {
algorithm hmac-sha256;
secret "HyvNbq6jTrtq/JVcUH3yBjHWduMxiKMCOX1tuBa/hOw=";
};
Contact Email: admin@example.com
ACME URL:
HTTPS Hostname: ntp1.example.com
DDNS Hostname: _acme-challenge.ntp1.example.com
Alt HTTPS Hostnames:
DDNS Nameserver: (automatic)
DDNS TSIG:
key "example-test" {
algorithm hmac-sha256;
secret "HyvNbq6jTrtq/JVcUH3yBjHWduMxiKMCOX1tuBa/hOw=";
};
Continue? [y/n]
Note that Dynamic updates to your zone are NOT required as static sub-delegation and CNAMEs are supported as long as those delegations point to a DNS zone that does support Dynamic updates. For example:
| DNS Entry | Type | Value | Dynamic/Static |
|---|---|---|---|
| ntp1.example.com | AAAA | 2001:db8:881:3::100 | Static |
| _acme-challenge.ntp1.example.com | CNAME | foobar.ddns-service.example.org | Static |
| foobar.ddns-service.example.org | TXT | (generated) | Dynamic |
Method? [H/D/M/q] D
To use Let's Encrypt DNS-01 method you will require:
* An administrative contact email address
* A public hostname for this device
* A public Dynamic DNS service (with or without TSIG)
* Outbound HTTPS to the Internet
For more information see the HTTPS docs at https://centerclick.com/ntp
Continue? [y/n] y
Contact Email: admin@example.com
HTTPS Hostname: ntp1.example.com
DDNS Hostname (if non-standard): foobar.ddns-service.example.org
DDNS Nameserver (if non-standard): nsupdate.ddns-service.example.org
Copy/Paste full DDNS TSIG key (if needed), use <CTRL-D> to finish:
key "example-test" {
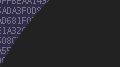
algorithm hmac-sha256;
secret "HyvNbq6jTrtq/JVcUH3yBjHWduMxiKMCOX1tuBa/hOw=";
};
Contact Email: admin@example.com
HTTPS Hostname: ntp1.example.com
DDNS Hostname: foobar.ddns-service.example.org
DDNS Nameserver: nsupdate.ddns-service.example.org
DDNS TSIG:
key "example-test" {
algorithm hmac-sha256;
secret "HyvNbq6jTrtq/JVcUH3yBjHWduMxiKMCOX1tuBa/hOw=";
};
Continue? [y/n]
By default, the DNS update will be sent to the name servers for the zone in question, however this can be overridden using the 'DDNS Nameserver' value. If a TSIG is provided, it will be used to authenticate with the DNS server.
Manual Upload
If all else fails, you can upload your own certificates, however you will need to repeat this process every time your certificates expire.
You will need to generate your own certificates off-box. You need 2 files:
- A Private Key in a file called privkey.pem having a single block starting with: -----BEGIN PRIVATE KEY-----
- A Certificate Chain in a file called fullchain.pem having multiple blocks each starting with: -----BEGIN CERTIFICATE-----
NOTE: Ideally the certificate file should contain the public certificates for the entire chain of trust from the device up through the root CA so it can be presented to the HTTPS client during TLS negotiation.
Method? [H/D/M/q] M To use manual certificate method you will require: * An off-box generated certificate key-chain and private key * Have uploaded these files using scp For more information see the HTTPS docs at https://centerclick.com/ntp ERROR: privkey.pem and fullchain.pem files not found.
The 2 files are not entered on the admin console. You need to SCP these in advance:
$ scp -O privkey.pem admin@ntp1.example.com:privkey.pem admin@ntp1.example.com's password: privkey.pem 100% 1708 459.4KB/s 00:00 $ scp -O fullchain.pem admin@ntp1.example.com:fullchain.pem admin@ntp1.example.com's password: fullchain.pem 100% 5620 1.3MB/s 00:00 $
NOTE: only specific SCP destinations are allowed, you must copy the files individually and to the exact destinations above. Once uploaded they will be detected:
Method? [H/D/M/q] M To use manual certificate method you will require: * An off-box generated certificate key-chain and private key * Have uploaded these files using scp For more information see the HTTPS docs at https://centerclick.com/ntp Found privkey.pem and fullchain.pem, installing...
Certificate Renewal
If you used either of the Let's Encrypt methods, renewals will occur automatically. The device will renew and install new certificates prior to the old one's expiration. NOTE: This assumes that the method used originally will still work on an ongoing basis. If your certificates fail to renew, Let's Encrypt will send an email to the admin contact entered when you registered.
If you used the manual upload method it is your responsibility to disable HTTPS, upload renewed certificates and re-enable HTTPS.
